Sandboxing
If you load a new app onto a smartphone with Android or iOS, this app is very restricted in its permissions. For example, to access the device’s memory outside the app, the user must first explicitly allow the app to do so. This opens a dialog that contains a message such as “[app name] is trying to access the memory” and two buttons with the options “allow” or “deny”. Such mechanisms are known as portals, as they form a gateway out of the app’s sandbox. A sandbox is a firmly defined area that is assigned to the app and which it is not allowed to cross without further ado. A security feature that can, for example, make it more difficult for malicious apps to access the data in the banking app installed next to it or the user’s private photos.
It is interesting to note that similar mechanisms have not found their way into our PC operating systems on a broad front since then. Microsoft Windows, for example, does not include such mechanisms in the home edition, even though there is an enterprise feature, Application Guard, which establishes a comparable protection mechanism. Such sandboxing mechanisms were also uncommon on Linux-based operating systems until a few years ago. Modules such as SELinux or AppArmor, which implement mandatory access control, i.e. access control to resources based on rules, have existed there for some time. SELinux is also what is used in Android for sandboxing apps (Android itself is based on Linux). Firejail](https://firejail.wordpress.com/) can also be used under Linux to “lock down” applications. The latter is used extensively in the Linux distribution Parrot Linux, for example, to start all installed applications with restrictions if desired.
These last points in particular are interesting for me personally, because I use Linux operating systems in my private life and I have a heightened need for security when it comes to IT, even for professional reasons. That’s why I’ve used Parrot Linux for years, to have the certainty that my browser, for example, can’t access the entire file system at will. Sandboxing via Firejail was merciless: When downloading a file in the browser, I could only save it in the “Downloads” folder. Attempts to access other folders in the download dialog were blocked. This made things very cumbersome in practice. Every time I wanted to place this file under “Documents”, for example, I first had to save it in the “Downloads” folder and then move it manually to “Documents” using the file manager. This inconvenience also led the developers of Parrot Linux at some point to disable the default starting of all applications in sandboxes and instead make starting in the sandbox optional.
However, the emergence of the new package formats “Snap” and “Flatpak” in the Linux landscape currently gives hope that more elegant, user-friendly ways of sandboxing are possible. The developers of the forward-looking Linux distribution elementaryOS are currently pushing ahead with a development that will result in a completely flatpak-based app marketplace whose applications will run in sandboxes with carefully designed portals. In conjunction with the fact that hardly any other Linux distribution attaches as much importance to user-friendliness as elementary, this seems very promising.
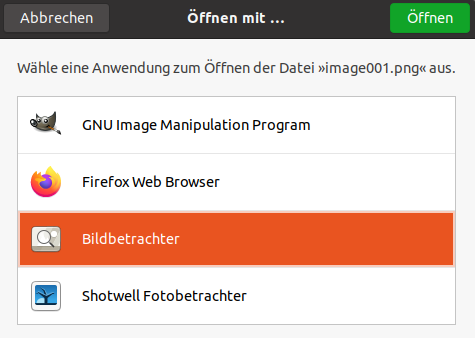
I recently switched from the pre-installed Firefox browser to the Flatpak version of the same browser on my Ubuntu computer to see how sandboxing would manifest itself there. And again it showed up in the file download process. In this case, the default location for storing downloaded files is not even the usual “Downloads” directory, but a folder within the Flatpak installation. Fortunately, it was also possible to select other folders outside the app directory - a big gain in usability compared to my experience with firejail under Parrot Linux. Even more interesting was the direct opening of a downloaded file. Instead of a list of installed applications, the “Open with” dialog known from downloads only contains the entry “System Handler”.
Download dialog Portal icon in Ubuntu 20.04 Portal window in Ubuntu 20.04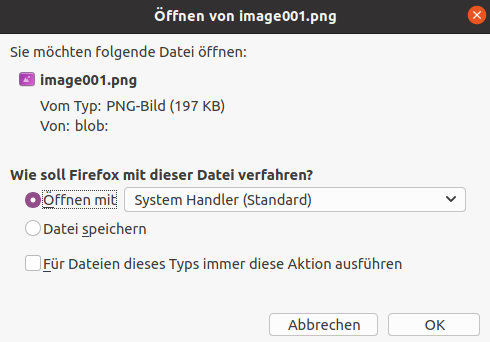
Sandboxing is an absolutely desirable feature for PC operating systems. The new Linux package formats show that this can also be implemented in a user-friendly way. It is to be hoped that this trend will also continue with Windows and other consumer operating systems.